DNA Synthesis Screening
DNA synthesis technologies are rapidly advancing and becoming more widely accessible, raising concerns about their potential misuse in the creation of harmful biological agents. Screening measures exist but remain fragmented and voluntary, leaving gaps that could be exploited, particularly given developments in AI that enable the design of novel pathogens. Strengthening security will require universal screening standards, international cooperation to update tools and practices, and robust cybersecurity in laboratories to safeguard against emerging biological and digital threats.
All living organisms, including those that can be used for malicious purposes, share one critical feature: their genomes are made of . Nucleic acids can be isolated from biological material and then sequenced, i.e., “read”. The outcome is a sequence of bases in a DNA fragment which can be used in applications from ancestry studies and human heritable disease analysis to biodefense or pandemic preparedness and response.
The increasing availability of pathogen genome sequences and high-throughput sequencing methods enables the detection of pathogenic microorganisms in complex environments. For example, using to analyze the total DNA from a sample allows for the identification of various microbial species and strains, e.g., for infectious disease surveillance. Sequencing methodologies also play a crucial role in microbial forensics, helping to determine the likely source and/or perpetrator(s) of a deliberate release.
From Reading to Writing: DNA Synthesis
DNA synthesis technology “prints” DNA, allowing researchers to engineer biological systems to gain insights into their functions. Synthetic DNA is used globally in bioscience laboratories and is essential for many biotechnological advancements, including agricultural products, pharmaceuticals, advanced fuels, and other biomanufacturing applications. DNA synthesis is a continuously growing industry, and today, almost everything in a molecular biology laboratory requires the ability to produce DNA fragments of specific lengths and sequences – a business that is reaching annual sales worth hundreds of millions of dollars.1
However, like any powerful tool, synthetic DNA carries risks, both accidental and intentional. Because viral genomes can be synthesized and activated into living viruses, a major concern is the potential release of engineered pathogens. At present, most synthetic DNA is provided by companies that have voluntarily implemented a screening system to mitigate this risk.
Many experts argue that next-generation benchtop DNA synthesis devices will make DNA synthesis more accessible to a broader range of users, including malicious actors, highlighting the need for a universal screening mechanism.
DNA (Synthesis) Screening
While screening nucleic acid synthesis orders is not yet mandated by any national government, DNA providers belonging to the International Gene Synthesis Consortium (IGSC) voluntarily screen both orders and customers to ensure that DNA containing potentially harmful sequences is not sold to individuals lacking a legitimate purpose. However, the Nuclear Threat Initiative think tank estimates that these companies make up only around 80% of the global market share. 2 The IGSC requires DNA synthesizers to screen every 200-(bp) sub-sequence using a best-match approach. Any suspicious sequences must undergo human inspection to ensure safety and legitimacy.
Methods to identify concerning sequences include database matching, where submitted sequences are compared against curated lists of known pathogens, toxins, and other high-risk elements; and machine learning approaches, which analyze patterns in sequence data to flag novel or engineered sequences with potentially harmful properties.

DNA Synthesis Order Screening Scenarios
DNA order screening needs to be both efficient and flexible, guided by shared standards from governments, international organizations, and industry, to balance security with scientific progress. In an ideal scenario, the order screening would also include Know Your Order (KYO) and Know Your Customer (KYC) practices similar to those in the banking industry. These steps could help ensure that both customers and orders undergo careful checks for any security risks. Establishing universal standards for such screening processes across all DNA synthesis providers would help create consistent oversight, reducing gaps that malicious actors could exploit.
Consider the fictional characters Alice and Bob, who have both submitted orders to a DNA synthesis company (adapted from J. Monrad, personal communication, February 22, 2025).3 Alice is a well-known scientist in Germany with over two decades of experience in vaccine development, including mRNA vaccines during the 2019 COVID-19 pandemic. She has now requested a synthetic DNA sequence that could potentially be adapted to her mRNA-based vaccines.
During the screening process, it would be correctly noted that Alice is a returning customer with a long track record of working with the same family of viruses for which she has requested the DNA fragments. In this scenario, despite the DNA sequence being flagged for additional checks due to its similarities with a potential pandemic pathogen (PPP), Alice would still be able to receive near-next-day service.
Now consider Bob, who has also submitted an order to the DNA synthesis company. Bob previously worked in a laboratory in Germany, where he completed his MSc, so he has significant knowledge of molecular engineering techniques. Over time, however, Bob has developed malicious worldviews and is attempting to create enhanced PPPs. In an ideal scenario, Bob’s order would be flagged just as Alice’s was. During the follow-up screening, it would be noted that Bob’s order was directed to a parcel box rather than an official laboratory, as was the case with Alice. Additionally, there are no publications or research grants under Bob’s name to justify his request for the DNA samples. As a result, the requested DNA orders would not be delivered to Bob.
We do not yet live in this ideal world, but significant advancements are being made. Researchers at institutions like the International Biosecurity and Biosafety Initiative (IBBIS)4 and SecureDNA5 are developing various DNA screening systems. The nucleic acid synthesis screening system from IBBIS uses a software tool that employs a range of methods to identify concerning sequences, match them with known pathogens, and confirm benign genes that can be approved for synthesis. The team at IBBIS has also published a report from their Customer Screening Working Group,6 proposing a system to verify legitimacy that could be used by various DNA providers and those providing benchtop DNA synthesis devices.
SecureDNA (https://securedna.org/) on the other hand, offers a free, privacy-preserving, and fully automated system designed to screen DNA synthesis orders of 30+ characters against a regularly updated hazard database. Its operational performance and specificity have been evaluated by providers in the United States, Europe, and China. As DNA synthesis technology becomes more accessible, cybersecurity in academic and commercial laboratories will be crucial to protect sequence data and prevent cyber-bio attacks that could compromise screening systems or enable unauthorized synthesis of harmful sequences.
None of these proposed measures offers a simple or complete solution. However, they aim to narrow the significant gap between the growing risks posed by advanced DNA technologies and the limited safeguards now in place to prevent accidents or misuse. The “Swiss cheese” model, often used in security contexts, illustrates how multiple layers of imperfect defenses together reduce the chance that threats slip through all gaps.
The Role of AI in DNA Synthesis Screening
Rapid advances in AI-assisted engineering are driving breakthroughs in the life sciences with numerous beneficial applications. However, these capabilities also introduce biosecurity risks by enabling the intentional or accidental synthesis of hazardous genes.
Until recently, biosecurity screening software solutions used by nucleic acid synthesis companies have primarily relied on detecting sequence similarities between ordered sequences and those unique to regulated toxins, viruses, or other organisms. This screening is intended to prevent the creation and spread of genes proteins of concern. Several research teams have been examining potential vulnerabilities in identity-based sequence screening, particularly in the context of AI-assisted protein design tools that diversify a protein’s amino acid sequence while preserving its function.7 Insights from this effort demonstrated that screening mechanisms could be improved to better detect AI-designed or synthetic variants of proteins of concern.8 This approach was inspired by the Computer Emergency Response Team (CERT) framework, developed by the cybersecurity community for handling threats involving previously unknown vulnerabilities. Given the rapid progress in AI capabilities and the global nature of synthetic biology, international collaboration frameworks are essential to keep screening tools updated and to audit them regularly. Such cooperation can help integrate AI-aware methods capable of identifying emerging synthetic threats more effectively.
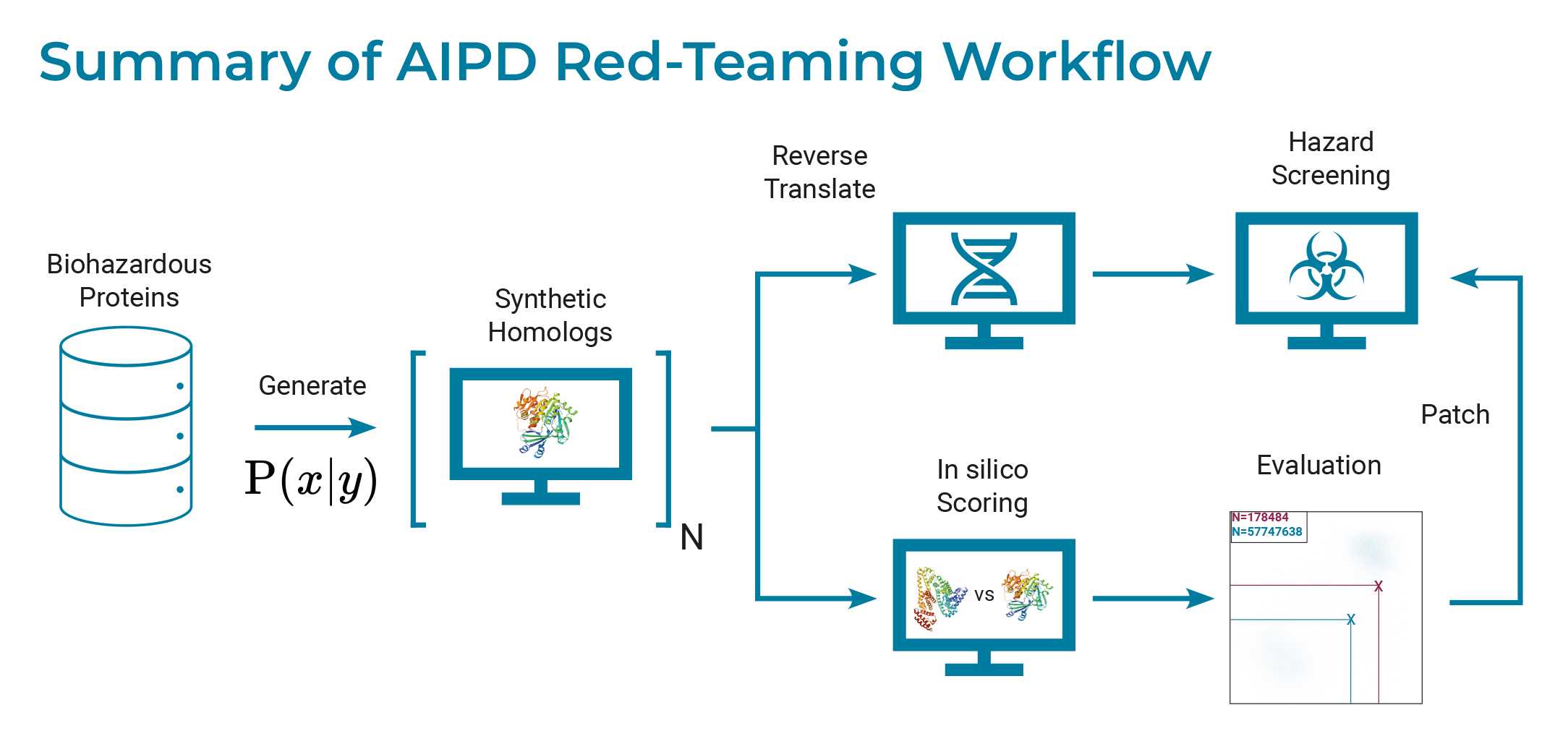
The U.S. Intelligence Advanced Research Projects Activity (IARPA) – a government agency that funds research into current and future intelligence problems – has also been running a project on functional genomic and computational threat assessment,9 with last updates from 2022. The project was set up to focus on methods to rapidly assess the function of potentially dangerous DNA sequences, aiming to detect both “bio-error” (unintended mistakes in biological research) and bio-terror.
Cybersecurity and DNA Synthesis
With the increasing accessibility of DNA synthesis, there is growing concern that a cyberattack interfering with synthetic DNA orders could result in the production of nucleic acids encoding components of pathogenic organisms, harmful proteins, or toxins.10 Such an attack could compromise the computer systems that process sequence orders, potentially allowing attackers to insert or alter DNA sequences, bypass screening protocols, thereby causing the synthesis of dangerous products without the knowledge of the user or synthesis provider. Most screening protocols require human inspection of suspicious sequences to verify safety and legitimacy. However, these follow-ups are costly and time-consuming. Without comprehensive penetration testing of screening frameworks, some pathogenic sequences may evade detection and bypass oversight. Experts argue that cyber-bio attacks are an overlooked threat, with many academic labs lacking cybersecurity infrastructure. In a realistic scenario, a toxic peptide-encoding DNA sequence could be concealed and evade detection by screening software.
As automation in biological laboratories advances, cyber threats are increasingly extending into the physical realm, crossing the boundary between the digital and physical worlds. Because DNA synthesis is often regarded as the ultimate control point between the digital and the physical, mitigating these risks is essential. Best practices and standards must be seamlessly incorporated into operational biological protocols to ensure security.
- Berry, D. J. (2019). Making DNA and its becoming an experimental commodity. History and Technology, 35(4), 374–404. https://doi.org/10.1080/07341512.2019.1694125 ↩
- Nuclear Threat Initiative (n. d.). Preventing the Misuse of DNA Synthesis Technology. Retrieved September 8, 2025, from https://www.nti.org/about/programs-projects/project/preventing-the-misuse-of-dna-synthesis-technology/ ↩
- Monrad, J. (2025, 22. Februar). Governing synthetic DNA to promote biosecurity and innovation [Personal communication]. ↩
- Wheeler, N. E., Carter, S. R., Alexanian, T., Isaac, C., Yassif, J., & Millet, P. (2024). Developing a Common Global Baseline for Nucleic Acid Synthesis Screening. Applied Biosafety, 29(2), 71–78. https://doi.org/10.1089/apb.2023.0034 ↩
- Baum, C., Berlips, J., Chen, W., Cui, H., Damgard, I., Dong, J., Esvelt, K. M., Foner, L., Gao, M., Gretton, D., Kysel, M., Li, J., Li, X., Paneth, O., Rivest, R. L., Sage-Ling, F., Shamir, A., Shen, Y., Sun, M., Vaikuntanathan, V., Van Hauwe, L., Vogel, T. Weinstein-Raun, B., Wang, Y., Wichs, D., Wooster, S., Yao, A. C., Yu, Y., Zhang, H., & Zhang, K. (2024). A system capable of verifiably and privately screening global DNA synthesis (Version 2). arXiv. https://doi.org/10.48550/ARXIV.2403.14023 ↩
- Alexanian, T., & Carter, S. R. (2024). Verifying legitimacy. Findings from the customer screening working group, 2020-2023. International Biosecurity and Biosafety Initiative for Science. https://ibbis.bio/wp-content/uploads/2024/02/IBBIS_Whitepaper_2024_Verifying_Customer_Legitimacy-1.pdf ↩
- Hunter, P. (2024). Security challenges by AI-assisted protein design: The ability to design proteins in silico could pose a new threat for biosecurity and biosafety. EMBO Reports, 25(5), 2168–2171. https://doi.org/10.1038/s44319-024-00124-7 ↩
- Wittmann, B. J., Alexanian, T., Bartling, C., Beal, J., Clove, A., Diggans, J., Flyangolts, K., Gemler, B. T., Mitchell, T., Murphy, S. T., Wheeler, N. E., & Horvitz, E. (2024). Towards AI-Resilient Screening of Nucleic Acid Synthesis Orders: Process, Results, and Recommendations. bioRxiv. https://doi.org/10.1101/2024.12.02.626439 ↩
- IARPA. (2022). Fun GCAT - Functional Genomic and Computational Assessment of Threats. https://www.iarpa.gov/images/PropsersDayPDFs/Fun-GCAT/fun_gcat_slicksheet_07202022.pdf ↩
- Puzis, R., Farbiash, D., Brodt, O., Elovici, Y., & Greenbaum, D. (2020). Increased cyber-biosecurity for DNA synthesis. Nature Biotechnology, 38(12), 1379–1381. https://doi.org/10.1038/s41587-020-00761-y ↩